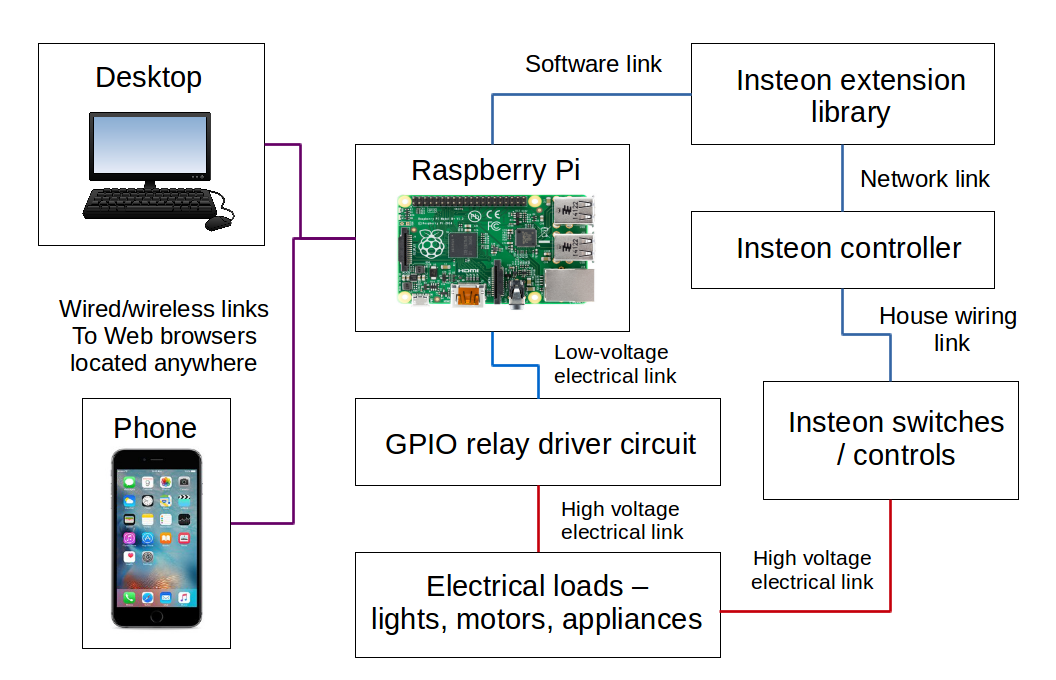
In the era of remote work and digital innovation, secure remote access has become an essential tool for individuals and businesses alike. Raspberry Pi secure remote access free solutions offer a cost-effective and customizable option to connect to your devices securely from anywhere in the world. Whether you're managing servers, accessing files, or controlling IoT devices, Raspberry Pi provides a powerful platform to achieve this.
As technology continues to evolve, so do the challenges of cybersecurity. With increasing threats to data privacy and network security, finding a reliable method to remotely access your systems is more important than ever. Raspberry Pi, a small yet powerful single-board computer, offers users the flexibility to set up secure remote access without breaking the bank.
This comprehensive guide will walk you through everything you need to know about Raspberry Pi secure remote access free setups. From installation and configuration to troubleshooting and optimization, we'll cover it all. By the end of this article, you'll have the knowledge and tools to implement a secure remote access solution tailored to your needs.
Read also:The Cast Of The Bernie Mac Show A Comprehensive Look At The Talented Ensemble
Table of Contents
- Introduction to Raspberry Pi Secure Remote Access
- Benefits of Using Raspberry Pi for Secure Remote Access
- Setting Up Raspberry Pi for Secure Remote Access
- Essential Tools for Raspberry Pi Secure Remote Access
- Methods for Raspberry Pi Secure Remote Access
- Enhancing Security for Raspberry Pi Remote Access
- Troubleshooting Common Issues
- Optimizing Raspberry Pi for Remote Access
- Comparing Raspberry Pi with Other Remote Access Solutions
- Conclusion and Next Steps
Introduction to Raspberry Pi Secure Remote Access
Raspberry Pi has revolutionized the way we approach technology by offering a compact and affordable single-board computer. One of its most valuable applications is secure remote access, enabling users to connect to their devices from anywhere securely. This section will introduce you to the basics of Raspberry Pi secure remote access and why it's a popular choice for tech enthusiasts and professionals.
What is Raspberry Pi Secure Remote Access?
Raspberry Pi secure remote access refers to the ability to connect to a Raspberry Pi device from a remote location using secure protocols. This setup allows users to manage files, run applications, and control devices as if they were physically present. The key to this functionality lies in the use of secure communication protocols such as SSH (Secure Shell) and VPN (Virtual Private Network).
Why Choose Raspberry Pi for Secure Remote Access?
There are several reasons why Raspberry Pi stands out as a top choice for secure remote access:
- Cost-Effective: Raspberry Pi is an affordable device that offers significant value for its price.
- Customizable: Users can tailor the setup to meet their specific needs and preferences.
- Community Support: A vast community of developers and enthusiasts provides resources and support for Raspberry Pi projects.
- Energy Efficient: Raspberry Pi consumes minimal power, making it ideal for long-term use.
Benefits of Using Raspberry Pi for Secure Remote Access
Beyond its affordability and flexibility, Raspberry Pi offers numerous benefits for secure remote access. Let's explore some of the key advantages:
Enhanced Security
With built-in support for secure protocols like SSH and SSL, Raspberry Pi ensures that your remote connections remain protected from unauthorized access. Additionally, you can implement advanced security measures such as firewalls and encryption to further safeguard your data.
Scalability
Raspberry Pi can be easily scaled to accommodate growing demands. Whether you're managing a single device or a network of IoT devices, Raspberry Pi can handle the workload efficiently.
Read also:Mila Kunis Feet A Comprehensive Exploration Of The Topic
Compatibility
Raspberry Pi supports a wide range of operating systems and software, making it compatible with various applications and tools. This versatility allows users to integrate Raspberry Pi into existing systems seamlessly.
Setting Up Raspberry Pi for Secure Remote Access
Setting up Raspberry Pi for secure remote access involves several steps, from initial configuration to implementing security measures. Follow this step-by-step guide to get started:
Step 1: Install the Operating System
Begin by installing a suitable operating system on your Raspberry Pi. Raspberry Pi OS is a popular choice due to its ease of use and extensive support for remote access tools.
Step 2: Enable SSH
SSH is a secure protocol that allows you to access your Raspberry Pi remotely. To enable SSH, follow these steps:
- Open the Raspberry Pi configuration tool.
- Navigate to the "Interfaces" tab.
- Select "SSH" and enable it.
Step 3: Configure Network Settings
Ensure that your Raspberry Pi is connected to the internet and has a static IP address. This will allow you to access it consistently from remote locations.
Essential Tools for Raspberry Pi Secure Remote Access
To implement secure remote access on Raspberry Pi, you'll need a few essential tools:
SSH Clients
SSH clients like PuTTY (for Windows) or Terminal (for macOS and Linux) allow you to connect to your Raspberry Pi securely. These tools provide a command-line interface for managing your device.
VPN Software
Using a VPN enhances the security of your remote connections by encrypting data transmitted between your device and the Raspberry Pi. OpenVPN is a popular choice for setting up a secure tunnel.
File Transfer Protocols
Tools like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol) enable secure file transfers between your local machine and Raspberry Pi.
Methods for Raspberry Pi Secure Remote Access
There are several methods to achieve secure remote access with Raspberry Pi. Below are some of the most common approaches:
Method 1: SSH
SSH is the simplest and most widely used method for remote access. It provides a secure and encrypted connection to your Raspberry Pi, allowing you to execute commands and manage files remotely.
Method 2: VNC (Virtual Network Computing)
VNC enables you to access the graphical user interface of your Raspberry Pi from a remote location. This method is ideal for tasks that require a visual interface.
Method 3: Web-Based Access
By setting up a web server on your Raspberry Pi, you can access it through a web browser. This method is useful for monitoring and controlling devices via a web interface.
Enhancing Security for Raspberry Pi Remote Access
Security is paramount when it comes to remote access. Here are some tips to enhance the security of your Raspberry Pi setup:
Use Strong Passwords
Ensure that all user accounts on your Raspberry Pi have strong, unique passwords. Avoid using default passwords and enable two-factor authentication if possible.
Implement Firewall Rules
A firewall can help protect your Raspberry Pi from unauthorized access by blocking unwanted traffic. Use tools like UFW (Uncomplicated Firewall) to configure firewall rules easily.
Regularly Update Software
Keep your Raspberry Pi's operating system and software up to date to protect against vulnerabilities and exploits. Regular updates ensure that your device remains secure.
Troubleshooting Common Issues
Despite careful setup and configuration, you may encounter issues with Raspberry Pi secure remote access. Here are some common problems and their solutions:
Problem 1: Unable to Connect via SSH
If you're unable to connect to your Raspberry Pi via SSH, check the following:
- Ensure that SSH is enabled on your Raspberry Pi.
- Verify that your Raspberry Pi is connected to the internet.
- Check the IP address and port number for accuracy.
Problem 2: Slow Connection Speeds
Slow connection speeds can be caused by network congestion or insufficient bandwidth. Consider upgrading your internet connection or using a wired connection for better performance.
Optimizing Raspberry Pi for Remote Access
To get the most out of your Raspberry Pi secure remote access setup, consider the following optimization tips:
Improve Network Performance
Optimize your network settings to ensure fast and reliable connections. Use tools like Wi-Fi analyzers to identify and resolve interference issues.
Automate Tasks
Automate repetitive tasks using scripts and cron jobs. This will save you time and reduce the need for constant manual intervention.
Comparing Raspberry Pi with Other Remote Access Solutions
While Raspberry Pi offers a compelling solution for secure remote access, it's essential to compare it with other options on the market:
Commercial Solutions
Commercial remote access solutions like TeamViewer and AnyDesk offer user-friendly interfaces and advanced features but come at a cost. Raspberry Pi provides a free alternative that can be customized to meet specific needs.
Cloud-Based Solutions
Cloud-based remote access solutions like AWS and Microsoft Azure offer scalability and reliability but may incur higher costs. Raspberry Pi is a cost-effective option for smaller-scale projects.
Conclusion and Next Steps
Raspberry Pi secure remote access free solutions provide a powerful and flexible way to connect to your devices from anywhere. By following the steps outlined in this guide, you can set up a secure and reliable remote access system tailored to your needs.
We encourage you to take action by experimenting with Raspberry Pi and exploring its capabilities. Leave a comment below to share your experiences or ask questions. Don't forget to explore other articles on our site for more insights into technology and innovation.
Thank you for reading, and happy tinkering!